Embark on a journey through the labyrinth of digital disruptions, where enigmatic cues beckon attention and prompt contemplation. In the realm of cyber interactions, an intriguing phenomenon emerges, catching the vigilant eye of digital custodians. Beyond the veil of routine operations, an undercurrent of uncertainty lurks, prompting the need for discernment and resolution.
Amidst the flux of virtual exchanges, a distinctive identifier, akin to a cryptographic fingerprint, garners scrutiny. A cascade of indicators, veiled in ambiguity, whispers tales of potential disruption. The orchestration of these peculiar signals forms the crux of a curious narrative, urging exploration and illumination.
Peer into the depths of this cryptic conundrum, where conventional notions of tranquility wane in the face of emergent complexities. Herein lies the essence of digital stewardship–a relentless pursuit of comprehension amidst the ever-shifting currents of online dynamics.
Understanding Anomalous Behavior Notification 8847fdf36f5414fc-LAX

Exploring the intricacies of irregular occurrences within the specified identification code zone prompts a deeper comprehension of the underlying events. This segment delves into deciphering the nuances of peculiar conduct alerts, shedding light on their significance and implications.
Upon receiving a notification regarding atypical actions, it becomes imperative to discern the context and potential ramifications. By dissecting the nature of these notifications, users gain insight into the underlying factors contributing to the flagged behaviors.
- Exploring the Contextual Landscape: Unraveling the circumstances surrounding the flagged occurrences unveils crucial insights into the environment in which they transpire.
- Deciphering Behavioral Patterns: Analyzing the behavioral trends associated with the identified code zone facilitates the identification of recurring anomalies and potential threat vectors.
- Evaluating Risk Magnitude: Assessing the severity and potential impact of flagged activities aids in prioritizing response strategies and resource allocation.
By fostering a comprehensive understanding of the anomalous behavior notification mechanism, stakeholders are better equipped to formulate proactive measures aimed at mitigating risks and safeguarding against potential threats.
Understanding the Triggers of Alert 8847fdf36f5414fc-LAX
Unraveling the Origins of Alert 8847fdf36f5414fc-LAX: Delve into the mechanisms that initiate the identification of potential irregularities within the system. Explore the intricate pathways that lead to the activation of this distinct alert, uncovering the nuanced factors that contribute to its manifestation.
Analyzing the Catalysts Behind Alert 8847fdf36f5414fc-LAX: Examine the myriad stimuli and conditions that converge to evoke the scrutiny of the monitoring system, prompting the generation of this notable notification. Investigate the array of circumstances and behaviors that serve as precursors to the emergence of this particular alert.
Exploring the Triggers of Alert 8847fdf36f5414fc-LAX: Navigate through the landscape of potential events and activities that set in motion the detection protocols, ultimately leading to the identification of suspicious occurrences. Uncover the diverse array of triggers that activate the vigilance mechanisms integral to the surveillance framework.
Why Addressing Unusual Behavior Matters

In today's interconnected digital landscape, it's imperative to acknowledge and respond to irregular actions swiftly and decisively. Instances of unexpected behavior, whether they stem from unauthorized access attempts, unusual login locations, or anomalous transaction patterns, can signify potential threats to security and integrity. By promptly addressing these deviations, organizations can mitigate risks, safeguard sensitive data, and uphold the trust of their stakeholders.
Recognizing and rectifying suspicious activities is not merely a matter of adherence to regulatory standards or industry best practices. It's a fundamental aspect of maintaining operational resilience and preserving reputation. Failure to address such anomalies can result in severe consequences, ranging from financial losses to reputational damage. Therefore, establishing robust protocols for identifying and responding to suspicious behavior is paramount in today's dynamic cybersecurity landscape.
Furthermore, timely intervention in response to unusual actions demonstrates an organization's commitment to proactive risk management and customer protection. It fosters a culture of vigilance and accountability, where every instance of anomalous behavior is treated with the seriousness it warrants. By prioritizing the detection and resolution of suspicious activities, businesses can fortify their defenses and fortify trust among their clientele.
Ultimately, the importance of addressing suspicious activity lies in its potential to safeguard assets, preserve reputation, and uphold the principles of security and trust in an increasingly interconnected world.
Common Triggers Behind Alert 8847fdf36f5414fc-LAX
In this section, we delve into the underlying factors contributing to the activation of Alert 8847fdf36f5414fc-LAX. Understanding these catalysts is crucial for discerning potential threats and fortifying security measures.
| Potential Cause | Description |
| Irregular Behavior Patterns | Instances where actions deviate from established norms, suggesting potential unauthorized access or malicious intent. |
| Unusual Access Points | Access attempts originating from atypical locations or devices, warranting scrutiny for possible breaches. |
| Abnormal Traffic Patterns | Anomalies in data flow, such as sudden spikes or unexpected patterns, indicating potential security breaches or system abuse. |
| Unauthorized Account Activities | Activities conducted without proper authorization, signaling potential account compromise or misuse. |
| Pattern of Failed Authentication Attempts | Repeated unsuccessful login attempts, hinting at brute-force attacks or credential theft. |
By recognizing these common triggers, organizations can proactively identify and mitigate security risks associated with Alert 8847fdf36f5414fc-LAX, bolstering their overall defense mechanisms.
Risks of Overlooking Unsettling Incidents - Try Again at a Later Time Resolvent

In the realm of digital vigilance, turning a blind eye to potentially dubious occurrences can usher in a host of perilous consequences. Failure to heed indications of suspicious activity jeopardizes the integrity and security of your digital ecosystem. Dismissing such warnings may inadvertently grant unauthorized entities unfettered access to sensitive information, paving the way for breaches and intrusions.
| 1. | Compromised Data Integrity: By disregarding alerts, there lies the peril of compromising the integrity of your data repositories. Unaddressed anomalies may gradually erode the trustworthiness and accuracy of stored information, impeding decision-making processes and tarnishing organizational credibility. |
| 2. | Vulnerability Exploitation: Unchecked suspicious activities serve as open invitations for malicious actors to exploit vulnerabilities within your digital infrastructure. Ignoring these indicators inadvertently provides assailants with an advantageous foothold to orchestrate cyber-attacks, leading to potential data breaches, financial losses, and reputational harm. |
| 3. | Regulatory Non-Compliance: Neglecting to address alerts indicative of questionable behavior may result in non-compliance with regulatory standards and legal obligations. Inaction in the face of potential threats may subject organizations to severe penalties, legal ramifications, and loss of stakeholder trust, exacerbating long-term operational challenges. |
| 4. | Erosion of Trust: Repeated disregard for suspicious activity alerts can precipitate a gradual erosion of trust among stakeholders, including clients, partners, and employees. Failure to prioritize the safeguarding of digital assets and sensitive information may engender skepticism regarding an organization's commitment to security and reliability. |
This HTML section outlines the risks associated with ignoring unsettling incidents, emphasizing the importance of addressing suspicious activities to mitigate potential harm to data integrity, vulnerability exploitation, regulatory compliance, and trust.
Approaches to Addressing 8847fdf36f5414fc-LAX Alert Concerns
In this section, we will explore various strategies aimed at managing and mitigating issues associated with the flagged incident identifier. By employing these methodologies, users can effectively tackle potential anomalies, ensuring the integrity and security of their systems.
- Investigate Anomaly Patterns: Delve into the irregularities exhibited within the system to discern underlying trends or patterns that may indicate potential threats.
- Analyze User Behavior: Scrutinize user activities and interactions within the system, identifying deviations from established norms or expected behaviors.
- Implement Proactive Monitoring: Establish robust monitoring mechanisms to preemptively detect suspicious activities, enabling prompt intervention and resolution.
- Enhance Authentication Protocols: Strengthen authentication procedures to fortify access controls and mitigate unauthorized entry or malicious activities.
- Employ Machine Learning Algorithms: Harness the power of machine learning algorithms to detect anomalous behaviors and patterns, facilitating early detection and response.
- Collaborate with Security Experts: Engage with cybersecurity professionals to gain insights and guidance on effectively addressing identified security concerns.
Leveraging Security Measures for Preventing Recurrence

Ensuring the perpetuation of a secure environment demands a strategic fusion of protective protocols and vigilant surveillance. In the wake of potential threats, fortification against future adversities becomes paramount. This section delineates proactive methodologies aimed at thwarting the reappearance of suspicious occurrences, thereby fostering resilience within the operational framework.
Heightened Vigilance: Cultivating a culture of heightened awareness serves as the cornerstone of preemptive defense. Empowering personnel with comprehensive training equips them with the acumen to discern anomalous activities, thus preempting potential breaches.
Implementing Robust Authentication: Bolstering authentication mechanisms fortifies the bulwark against unauthorized access. Deploying multifactor authentication and dynamic password protocols erect formidable barriers, deterring nefarious actors from infiltrating the system.
Continuous Monitoring: Embracing a stance of perpetual vigilance entails the deployment of sophisticated monitoring systems. Real-time surveillance coupled with anomaly detection algorithms furnishes an early warning system, enabling swift intervention in the event of suspicious behavior.
Adopting Proactive Response Strategies: Proactivity in addressing security lapses is instrumental in averting potential crises. Instituting rapid response protocols and conducting routine drills ensures readiness to counter emergent threats effectively.
Regular Security Audits: Conducting periodic assessments evaluates the efficacy of existing security measures and identifies areas susceptible to exploitation. Iterative refinement based on audit findings fortifies the resilience of the system against evolving threats.
Cultivating a Culture of Security: Inculcating a collective consciousness regarding security imperatives fosters a cohesive defense posture. Encouraging stakeholder participation and fostering a sense of ownership engenders a robust communal ethos, wherein each individual becomes a sentinel in safeguarding organizational integrity.
Engaging Security Experts for Collaborative Support
When confronting unusual occurrences in your digital environment, it's often beneficial to seek guidance from those well-versed in the intricacies of security. This section explores the value of collaborating with knowledgeable professionals to address and mitigate potential threats effectively.
Partnering for Insight: Embracing the expertise of security specialists can furnish invaluable insights into deciphering and rectifying intricate security challenges. By fostering collaborative relationships, organizations can access a wealth of knowledge and experience, enhancing their ability to navigate complex security landscapes.
Harnessing Diverse Perspectives: Engaging with security experts facilitates the integration of diverse viewpoints, enriching problem-solving processes. Through open dialogue and shared analysis, teams can uncover unconventional solutions and anticipate emerging threats, bolstering their overall resilience.
Leveraging Specialized Skills: Security professionals possess specialized skills honed through rigorous training and hands-on experience. Leveraging these competencies empowers organizations to address security incidents promptly and decisively, minimizing potential disruptions and safeguarding vital assets.
Cultivating Continuous Improvement: Collaborating with security experts fosters a culture of continuous improvement, where proactive measures are prioritized over reactive responses. By actively engaging with industry leaders and staying abreast of evolving best practices, organizations can fortify their defenses and adapt to evolving security landscapes.
Conclusion: In the realm of cybersecurity, collaboration with security experts emerges as a cornerstone of effective risk management strategies. By leveraging collective knowledge, diverse perspectives, and specialized skills, organizations can navigate security challenges with confidence, ensuring the integrity and resilience of their digital assets.
Evaluating System Vulnerabilities and Enhancements
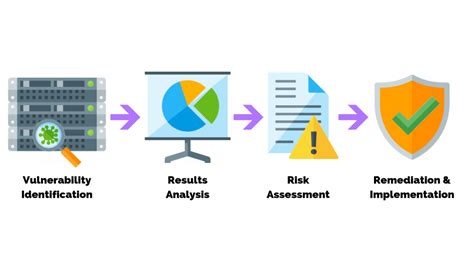
Exploring System Weaknesses and Advancements
Within the realm of system integrity and optimization lies a crucial task: the comprehensive evaluation of vulnerabilities and potential improvements. This section delves into the intricate process of dissecting system susceptibilities and strategizing enhancements without compromising system stability.
Identifying System Fragilities
An integral facet of fortifying any system involves pinpointing its susceptibilities–those subtle chinks in the armor that malevolent entities exploit. By discerning these vulnerabilities, we empower ourselves to erect robust defenses against unforeseen assaults.
Analyzing Paths to Enhancement
Enhancements, the bedrock of system fortification, demand meticulous scrutiny. Through rigorous analysis and innovative ideation, we unearth pathways to bolster system resilience and efficiency. From patching vulnerabilities to optimizing performance, each enhancement constitutes a strategic stride towards system fortitude.
Evaluating Risk Mitigation Strategies
Central to the evaluation process is the formulation and assessment of risk mitigation strategies. By weighing the potential impact of threats against the efficacy of proposed countermeasures, we navigate the intricate landscape of system security with prudence and precision.
Implementing Sustainable Solutions
Ultimately, the culmination of our evaluations manifests in the implementation of sustainable solutions. Through iterative refinement and proactive vigilance, we ensure that our systems evolve in tandem with emerging threats, fortifying their resilience in an ever-changing digital ecosystem.
Continuous Vigilance and Response Assurance
In the pursuit of maintaining utmost security and safeguarding against potential threats, it is imperative to establish a framework of continual monitoring and swift response measures. This section delves into the pivotal strategies and practices aimed at perpetually ensuring the integrity of operations, without interruption.
Central to this approach is the cultivation of a proactive mindset, wherein a dynamic array of techniques is employed to detect and address any anomalous occurrences that may undermine the security posture. By embracing a stance of perpetual vigilance, organizations can fortify their defenses against nefarious activities and swiftly mitigate emerging risks.
Furthermore, the establishment of robust protocols for real-time incident response forms a cornerstone of this enduring vigilance. Through the seamless integration of automated detection systems and human expertise, organizations can effectively thwart potential threats and maintain operational continuity in the face of adversity.
Moreover, the significance of ongoing analysis and refinement cannot be overstated in the quest for perpetual security assurance. By continuously evaluating existing processes and adapting to evolving threat landscapes, entities can enhance their resilience and ensure that their defenses remain agile and adaptive.
In essence, by prioritizing continual monitoring and response capabilities, organizations can uphold the integrity of their operations and navigate the complexities of the digital landscape with confidence and resilience.
FAQ
What does the Suspicious Activity Alert 8847fdf36f5414fc-LAX mean?
The Suspicious Activity Alert 8847fdf36f5414fc-LAX typically indicates that there has been unusual or potentially fraudulent activity detected on a particular account or service. It's a security measure to protect against unauthorized access or malicious actions.
Why am I seeing the Retry Later Solution for Suspicious Activity Alert 8847fdf36f5414fc-LAX?
The Retry Later Solution for the Suspicious Activity Alert 8847fdf36f5414fc-LAX indicates that the system encountered a potential security issue but couldn't resolve it immediately. It suggests waiting and trying again later as a precautionary measure while the system addresses the issue.
How serious is the Suspicious Activity Alert 8847fdf36f5414fc-LAX?
The seriousness of the Suspicious Activity Alert 8847fdf36f5414fc-LAX depends on various factors such as the nature of the activity detected and the sensitivity of the account or service involved. While it's important to address it promptly, not all instances may pose significant threats.
What should I do if I receive the Suspicious Activity Alert 8847fdf36f5414fc-LAX?
If you receive the Suspicious Activity Alert 8847fdf36f5414fc-LAX, it's essential to follow the recommended steps provided by the alert system or the service provider. This may involve verifying your identity, reviewing recent account activity, or contacting customer support for further assistance.
Is there a way to prevent getting the Suspicious Activity Alert 8847fdf36f5414fc-LAX in the future?
While it's not always possible to completely prevent Suspicious Activity Alerts like 8847fdf36f5414fc-LAX, there are several proactive measures you can take to enhance your account security. These include using strong, unique passwords, enabling two-factor authentication, and regularly monitoring your account for any unusual activity.
What is the Suspicious Activity Alert 8847fdf36f5414fc-LAX?
The Suspicious Activity Alert 8847fdf36f5414fc-LAX is a notification triggered by a security system indicating potentially unauthorized or irregular activity associated with a specific identifier or location.



